Maintaining your vehicle’s health is essential for ensuring a smooth and safe driving experience. One critical but often overlooked aspect of car maintenance is regular wheel alignment. This straightforward service can significantly impact your vehicle’s performance, safety, and longevity. In this blog, we’ll delve into the numerous benefits of regular wheel alignment and why it should be a priority in your vehicle maintenance routine.
1. Enhanced Driving Safety
Proper wheel alignment ensures that your vehicle handles correctly, which is crucial for your safety. Misaligned wheels can cause your car to pull to one side, making it challenging to steer, especially in emergency situations. Regular alignment checks ensure that your wheels are parallel and that your tires meet the road at the correct angle, providing better control and stability.
2. Improved Fuel Efficiency
Did you know that misaligned wheels can reduce your vehicle’s fuel efficiency? When wheels are out of alignment, your engine has to work harder to move the car forward, which increases fuel consumption. By keeping your wheels properly aligned, you can reduce rolling resistance and improve your car’s fuel efficiency, saving you money at the pump.
3. Extended Tire Lifespan
Tires are a significant investment for any vehicle owner. Misaligned wheels can cause uneven tire wear, leading to premature tire replacement. Regular wheel alignment ensures that your tires wear evenly, extending their lifespan and saving you the cost of frequent replacements. This not only benefits your wallet but also reduces the environmental impact of tire disposal.
4. Enhanced Driving Comfort
Misaligned wheels can cause vibrations and an uncomfortable ride. You might notice your steering wheel vibrating or your car shaking at certain speeds. Proper wheel alignment ensures a smoother, more comfortable ride by reducing these unwanted vibrations and improving overall vehicle stability.
5. Reduced Wear on Suspension and Steering Systems
Your vehicle’s suspension and steering systems are designed to work optimally with properly aligned wheels. Misalignment can place additional stress on these components, leading to accelerated wear and potential damage. Regular wheel alignment helps maintain the integrity of your suspension and steering systems, reducing the likelihood of costly repairs.
6. Better Handling and Performance
If you’re a driving enthusiast, you know the importance of precise handling and optimal vehicle performance. Proper wheel alignment ensures that your tires have maximum contact with the road, enhancing grip and responsiveness. This can be particularly beneficial in challenging driving conditions, such as wet or icy roads.
7. Prevention of Costly Repairs
Regular wheel alignment can help identify and address potential issues before they become significant problems. By catching misalignment early, you can prevent more severe damage to your vehicle’s tires, suspension, and steering systems. This proactive approach can save you from expensive repairs down the road.
When to Check Your Wheel Alignment
It’s recommended to check your wheel alignment every 6,000 miles or as specified in your vehicle’s owner’s manual. Additionally, you should have your alignment checked if you notice any of the following signs:
• Your vehicle pulls to one side.
• Uneven tire wear.
• Vibrations in the steering wheel.
• The steering wheel is off-center when driving straight.
• After hitting a curb or pothole.
Conclusion
Regular wheel alignment is a crucial aspect of vehicle maintenance that offers numerous benefits, from improved safety and fuel efficiency to extended tire lifespan and enhanced driving comfort. By making wheel alignment a regular part of your maintenance routine, you can enjoy a smoother, safer, and more cost-effective driving experience. Don’t wait for signs of misalignment to appear schedule your alignment check today and keep your vehicle running at its best.
Thanks for giving your valuable time to read this blog, In case you are having brand car for example Chevrolet and you are looking for a Chevrolet Service Center in Dubai then visit Service My Car website in case you need any service or repairs.
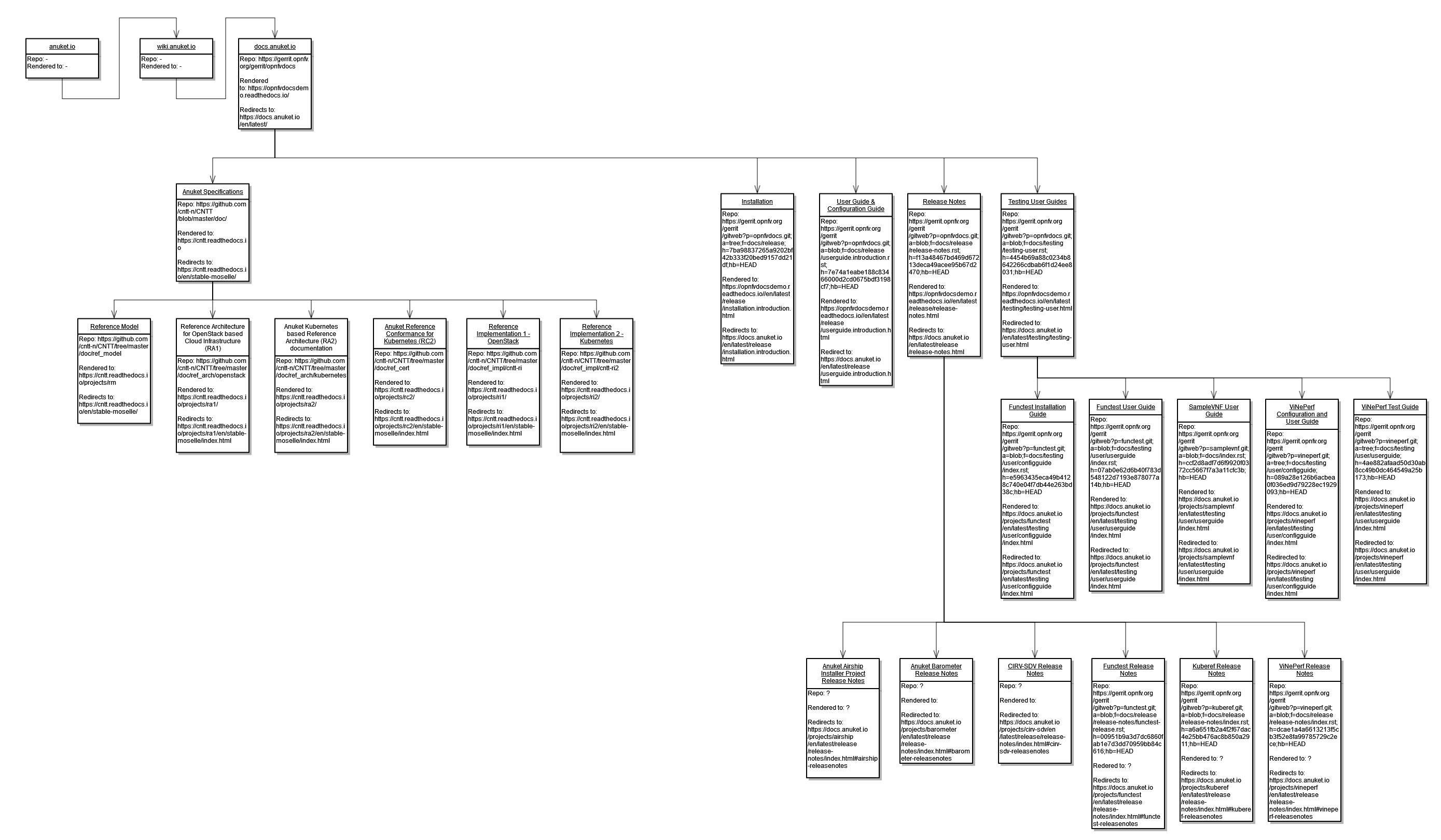
The Anuket team is pleased to announce that Pieman, the latest release of Anuket, a mature LF Networking project focused on reference models, architectures and testing tools, released May 14 2024 includes guidance for sustainability and closer alignment with the CNCF for Cloud Native infrastructures.
Anuket occupies a unique position in the telecom industry because it takes into consideration both operator and vendor requirements, having subject matter expert representatives who are very cognizant of the “real world” challenges of the industry. Anuket is being adopted as the reference infrastructure for other open source projects such as Sylva as well as part of the GSMA permanent document Reference Model as NG.126, Reference Architecture 2 (Kubernetes based) as NG.139, and Reference Architecture 1 (OpenStack based) as NG.133.
Reference Model (RM ) highlights include:
- Updated contents in Hardware Infrastructure Manager section, aligning and referencing the Redfish standard. Prior to Pieman, Hardware Infrastructure Manager existed in RM as a concept only. Now, it can be implemented, e.g., using ODIM as a basis.
- Added load balancer into RM technology agnostic definition, aligned to RA2 PR #3415 . It is based on a functional description, not on a specific implementation as typical load balancer technologies are defined.
- Started a technology agnostic guidance section to assist in planning more efficient open source based cloud infrastructure energy consumption. The RM focus is on the energy efficiency of the workload/infrastructure/management interactions. Energy savings are becoming a major issue for the telecom industry, with the massive use of data, energy efficiency and sustainability in the Hybrid, Multi-Cloud environment needs a consolidated approach by the ecosystem players.
- Added section on automated TLS certificate lifecycle management for workloads (from the infrastructure perspective).
Reference Architecture 2 ( RA2 ) The RA2 project focuses on building a Kubernetes based architecture that now been consolidated into the most comprehensive industry wide set of specifications for Kubernetes Telco Cloud - acceptance as a GSMA standard is confirming this status.
- Added Express Data Path (AF_XDP) network acceleration specs, enabling faster and more efficient data plane traffic processing. This provides an agreed network acceleration implementation, which benefits all users with containerised data plane functions
- Update to Kubernetes 1.29, including API specs and new functionality. Since PaaS services are essential operational add-ons to Kubernetes, which implement containerised network function monitoring, logging, traffic steering, etc.
- Add cert-manager for TLS certificate lifecycle management. A number of network functions require TLS certificates, this plugin allows management of their lifecycle automatically
- Add Load Balancer specs, for ingress traffic distribution across microservices. Load balancers steer traffic across the pods that compose containerised network functions. RA2 is specifying what is required of a load balancer to integrate with a Kubernetes based Telco cloud.
Anuket Overview
Anuket projects and work streams continued their efforts to strengthen container-based open infrastructure specifications and implementations. Some of other active projects include:
- Kubref - Project objectives is to develop and deliver a Kubernetes-based reference implementation according to the RA2 specifications in close collaboration with the RI2 and RC2 projects.
- Thoth – Team is working to define a set of anonymized data models for AI, intelligent networking decision-making problems.
- Functest, functest-kubernetes -- A suite of functional tests for OpenStack and Kubernetes deployments, now includes support for CNTi Testsuite.
Who is interested?
- Gergely Csatari (gergely.csatari@nokia.com) Phone: +358-40-358-0991
- Beth Cohen (beth.cohen@verizon.com)
- Lincoln Lavoie lylavoie@iol.unh.edu, Mobile Phone: +1-603-674-2755
More information here
- Anuket resources are very thin so hard to get anyone to work on the project
- Review of the project within Anuket – Some do not need release managers (Thoth), Some are not active, Some need releases (Functest, VinePerf, CIRV, Kuberef) and finally the reference docs.
- TSC could serve as a release manager with a stronger community
- We should support projects which do not follow the Anuket release model
- There are different categories of the projects
- Projects that do not need releases (Thoth)
- Inactive projects should just be archived
- Reference docs – need minimal release support (set dates and gather requirements)
- Set the dates for the release - TSC
- Release plan - sub-project teams/PTL
- Release tags in Jira and GitHub - TSC
- Associate Issues with the GitHub project plan - PTL
- Proofreading - PTL
- Release branch creation - TSC
- Readthedocs branch creation - TSC
- Sub-project release highlights - PTL
- Blogpost, release announcement - TSC
- Test projects
- Set the dates for the release - TSC
- Release plan - sub-project teams/PTL
- Release tags in Jira and GitHub - TSC
- Associate Issues with the GitHub project plan - PTL
- Documentation done - PTL/Team
- Keep two releases per year
- Update the release framework tasks with the slimmed down version
- Next steps:
- Gergely Csatari Propose a new release process template based on this: Orinoco Release Progress
This page collects the CNF requirements in RA2, RC2 and in CNCF CNF Conformance / CNF Testbed.
The original analyzis page for introducing the CNF requirements in RA2: Analyzis of CNCF CNF Testsuite tests for RA2
pr-s
| CNF Testsuite | CNF Conformance | RA2 | RA2 | RC2 | What to do? |
|---|---|---|---|---|---|
increase_decrease_capacity | essential | ra2.app.038 | should → must (3352) | should | Add a link to CNF Testsuite. Make a must in RA2 and RC2 |
helm_chart_published | ra2.app.011 | must | should | ||
helm_chart_valid | ra2.app.012 | must | should | ||
helm_deploy | |||||
rollback | |||||
rolling_update | ra2.app.013 | must | must | ||
rolling_version_change | |||||
rolling_downgrade | ra2.app.014 | must | must | ||
cni_compatibility | ra2.app.015 | must | must | ||
alpha_k8s_apis | ra2.app.016 | must (not) | must (not) | ||
reasonable_image_size | ra2.app.039 | should (not) | should (not) | ||
reasonable_startup_time | ra2.app.040 | should (not) | should (not) | ||
single_process_type | essential | missing | misssing | It is unclear if this is a realistic requirement. There is an ongoing discussion in CNF Testsuite about this. I propose to leave this out until this is clarified. | |
service_discovery | |||||
shared_database | |||||
specialized_init_systems | |||||
node_drain | essential | ra2.app.017 | must (not) | must (not) | |
volume_hostpath_not_found | |||||
no_local_volume_configuration | ra2.app.025 | must (not) | must (not) | ||
elastic_volumes | |||||
database_persistence | |||||
pod_network_latency | ra2.app.018 | must (not) | must (not) | ||
disk_fill | |||||
pod_delete | ra2.app.019 | must (not) | must (not) | ||
pod_memory_hog | ra2.app.020 | must (not) | must (not) | ||
pod_io_stress | ra2.app.021 | must (not) | must (not) | ||
pod_network_corruption | ra2.app.022 | must (not) | must (not) | ||
pod_network_duplication | ra2.app.023 | must (not) | must (not) | ||
pod_dns_errors | ra2.app.024 | must (not) | must (not) | ||
liveness | essential | ra2.app.026 | must | must | |
readiness | essential | ra2.app.027 | must | must | |
log_output | essential | ra2.app.046 | should → must (3352) | missing | Change it to must in RA2, add to RC2 |
prometheus_traffic | |||||
routed_logs | |||||
open_metrics | |||||
tracing | |||||
container_sock_mounts | essential | ra2.app.028 | must (not) | must (not) | Add reference to CNF Testbed to RA2 |
privileged_containers | essential | ra2.app.041 | should → must (3352) | should (not) | Change it to must RA2 and RC2. |
external_ips | |||||
non_root_user | ra2.app.042 | should | should (not) | Change it to must RA2 and RC2. | |
privilege_escalation | ra2.app.043 | should | should (not) | ||
symlink_file_system | |||||
selinux_options | essential | ra2.app.048 | must | missing | Add to RC2 |
sysctls | |||||
application_credentials | ra2.app.029 | must (not) | must (not) | ||
host_network | ra2.app.030 | must (not) | must (not) | ||
service_account_mapping | |||||
ingress_egress_blocked | |||||
insecure_capabilities | |||||
non_root_containers | essential | ra2.app.044 | should → must (3352) | should | Change to must in RA2, add to RC2 |
host_pid_ipc_privileges | ra2.app.031 | must (not) | must (not) | ||
linux_hardening | |||||
resource_policies | essential | ra2.app.032 | must | must (not) | |
immutable_file_systems | ra2.app.033 | must | must (not) | ||
hostpath_mounts | essential | ra2.app.007 | should (not) | should | Change to must in RA2, add to RC2 |
default_namespace | |||||
latest_tag | essential | ra2.app.049 ra2.app.034 | should (not) must (not) | 034: must | remove ra2.app.049 |
required_labels | ra2.app.045 | should | should | ||
versioned_tag | |||||
nodeport_not_used | ra2.app.036 | must (not) | must (not) | ||
hostport_not_used | essential | ra2.app.047 | should (not) → must (3352) | missing | Make it must in RA2, add to RC2 |
hardcoded_ip_addresses_in_k8s_runtime_configuration | essential | ra2.app.035 | must (not) | must (not) | |
secrets_used | |||||
immutable_configmap | ra2.app.037 | must | must | ||
| ra2.app.034 | must | ||||
| ra2.app.038 | should | should | |||
| ra2.app.001 | ??? → remove (3352) | must | It is not really clear what this requirement is and it is not tested in CNF Testbed I propose to remove this. | ||
| ra2.app.002 | ??? → remove (3352) | must | It is not clear what is the requirement here. Is this about host mounts? This is not tested by CNF Testbed I propose to remove this | ||
| ra2.app.003 | ??? → remove (3352) | must | It is not clear what is the requirement here. This is not tested by CNF Testbed I propose to remove this | ||
| ra2.app.004 | ??? → remove (3352) | must | It is not clear what is the requirement here. Kubernetes sets the pod name by default. This is not tested by CNF Testbed I propose to remove this. | ||
| ra2.app.005 | ??? → remove (3352) | must | It is not really clear what this requirement is and it is not tested in CNF Testbed I propose to remove this. | ||
| ra2.app.006 | must | must | |||
| ra2.app.007 | should (not) | must | |||
| ra2.app.008 | must (not) | must (not) | |||
| ra2.app.009 | must | must | |||
| ra2.app.010 | must | must | This in a littlebit of contradiction with ra2.app.016 I propose to modify it to a should. |
Nile, the latest version of Anuket was released to the public on January 4, 2023, with add cloud native requirements and testing functionality!
Anuket Overview
Anuket is an LF Networking project occupies a unique position in the telecom industry incorporating both operator infrastructure specifications, implementations, and open source infrastructure test suite development, all under a single initiative. The community has subject matter expert representatives from telco operators and their technology suppliers, which means that it is well positioned to address the “real world” challenges of the telecommunications industry. If you or anyone you know would like to contribute to any of these important activities, the Anuket website is a great place to start.
Leadership
Anuket members, per its Charter, elected the 2023 Technology Steering Committee and Co-chairs: Scott Steele and Gergely Csatari. On behalf of outgoing 2022 TSC Co-chairs, Gergely and myself, we would like to thank all Anuket contributors for their fantastic efforts in 2022 and wish the new TSC and the new Co-chairs all the best in their 2023 work!
Anuket Nile Release
Numerous Anuket projects and work streams continued to strengthen container-based open infrastructure specifications and implementations – an area that is increasingly important to the telco industry. Some of the accomplishments include:
- ViNePerf - The ViNePerf project continued development efforts to automate test setup and benchmarking of container networking with various CNI plug-ins (Multus, Cillium) and kernel acceleration (AF_XDP, eBPF), with the help of a Student Volunteer and an Intern from the LFN program.
- Thoth - The Thoth project continues to focus on implementing E2E AI for NFV use case scenarios. The newly established NICIP project is a jointly organized data generation competition with ITU. Thoth is also cooperating on AI frameworks such as Mindspore, and starting the R&D effort needed to create data anonymization tools to allow telecom companies to share without the fear of exposing actual customer data.
On the requirements side
- Reference Model (RM) changes (major):
- Infrastructure LCM Automation – re-edited and updated to improve readability and to ensure alignment with multi-cloud models
- Security sections updated to reflect (and refer to) evolving 5G security standards and best practices
- Added energy consumption metrics and related requirements
- Reference Architecture 1 (RA1) OpenStack changes:
- New chapter based on RC1 content integrates conformance and establishes the link between architecture requirements and tests, providing the mechanism to validate the cloud infrastructure against the set of defined requirements.
- Chapter 1 has been restructured with the addition of a bibliography and an abbreviations table.
- The whole document has been reviewed to ease the creation of version 2 of NG.133 GSMA document.
- 133 v2 has been officially published the 9thof December.
- Updates have been made for the support of containerized applicationsand Cyborg accelerators drivers.
- Reference Conformance 2 (RC2) has been updated to align with the latest versions of Kubernetes and Functest.
- Added specific test references supporting workloads by referencing the CNCF CNF testsuite.
In the coming releases, Hybrid, Multi-Cloud model and AI/ML utilisation, will be the focus of Anuket work in the upcoming releases, reflecting a growing global interest in more sophisticated operating models for telecommunication operators facing the challenges of real-life 5G/Edge/IoT implementations.
| Name | Earliest time to start the TSC in UTC | Latest time to start the TSC in UTC | Meeting Window in Hours |
|---|---|---|---|
| 8:00 | 16:00 | 8 | |
| 12:00 (if needed), 13:00 (preferred) | 01:00 +1 | 12 | |
| Pankaj Goyal | 14:00 | 0500 +1 | 15 |
| 12:00 | 16:00 | 15 | |
| 1:00 | 15:00 | 14 | |
| Georg Kunz | 08:00 | 16:00 | 8 |
| Walter Kozlowski | 20:00 (21:00 April - Oct) | 13:00 (next day) (14:00 April - Oct) | 17 |
In 2022, the Anuket Project continued its two release cadence with Moselle delivered in June and Nile following in December. As has been true for the last few years, Anuket has been focused on developing reference models, architectures and specifications in support of infrastructure for virtualized (CNF/VNF) telecom workloads. The requirements have continued to evolve to cover more use cases in the Reference Model (RM), and align these use cases with changes in upstream communities in the Reference Architectures for OpenStack (RA1) and Kubernetes (RA2). The application requirement specification for the Reference Architecture for Kubernetes matches with the CNCF CNF Conformance program to avoid the fragmentation of conformance programs in the industry, while fostering continued collaboration with the CNCF community. Taking the Reference Model and the Reference Architecture for OpenStack, in 2022 the Reference Conformance for OpenStack has also been released as a GSMA Permanent Release document. We are working with the GSMA on a planned release of the Reference Architecture for Kubernetes (RA2) in 2023. On top of the enhancement of collaboration with GSMA we plan to continue to evolve our specifications by adding new use cases, aligning with adjacent communities, such as Nephio, O-RAN and Sylva, and further increase the quality and coverage of our Reference Architecture for Kubernetes and conformance projects.
On the testing side of the project, Functest, the testing framework that supports the conformance and Anuket Assured programs maintains continuous release updates in synch with the upstream OpenStack and Kubernetes releases. The ViNePerf project continued development efforts to automate test setup and benchmarking of container networking with various CNI plug-ins (Multus, Cillium) and kernel acceleration (AF_XDP, eBPF), with the help of a Student Volunteer and an Intern from the LF program.
We also plan to continue the work we started in 2022 to increase the consumability of our project and our deliverables by enhancing our documentation, testing tools and web presence.
Intro
The target of this conspiracy to make Anuket more easy to understand for someone who is not involved in the project.
We would like to achieve this by tuning the already existing documentation created for the project. This includes applying consistent templates, linking the documents together in a meaningful way and many more listed in here.
This page is created to help the conspirators.
Current conspirators
Project management and communication
- GitHub project: https://github.com/cntt-n/CNTT/projects/34#card-85674686
- Meetings: we do not have a dedicated meeting, but use the Anuket Weekly Technical Discussions to discuss
- Communication: the common denominator is sending an email to the Current conspirators. If the issue is relevant for wider audience use the anuket-tech-discuss dl.
What is where